The latest 2015 Verizon Breach Investigation Report (VBIR) is now out and can be downloaded HERE. For those that have not seen these reports, they survey a number of customers and gather information about different types of breaches. It is a trend based report but great data to get an idea of which types of attacks are being seen by different types of businesses.
This year’s report has on the cover page “$400 Million. The estimated financial loss from 700 million compromised records shows the real importance of managing data breach risks”. The data comes from 70 organizations from 61 different countries that were interviewed showcasing 2,122 breaches. The report highlights that of 21 industries (including a unknown category) the same three industries have made the top of the list. The top three industry impacted by breaches were Public (50,315 incidents / 303 data loss events), Information (1,496 incidents / 95 data loss events) and Financial Services (642 incidents / 277 data loss events).
The time to compromise is still quick with claims “60% of cases show attackers are able to compromise an organization within minutes”. And example of a tactic used by attackers shown in the report is Phishing attacks where “23% of recipients opened phishing messages and 11% clicked on attachments”. My mom wasn’t interviewed but would be part of this number if she was included. She clicks anything!
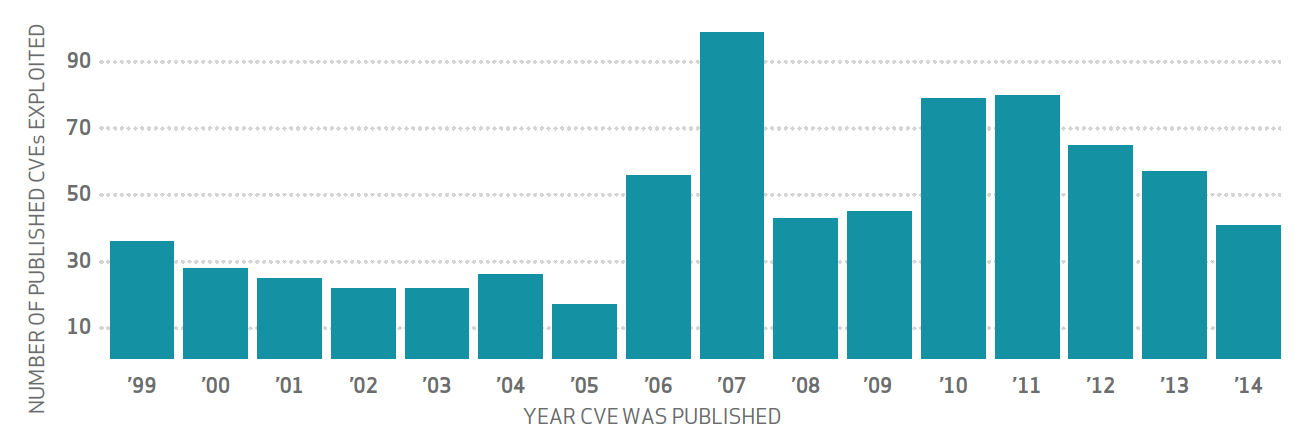
Regarding patching, the Verizon report shows 99.9% of the exploited vulnerabilities were compromised more than a year after the CVE was published! Wow thats just crazy to see organizations not keeping up with patch management or more likely just focusing on the latest threats rather than having a broader range of scanning. There are even vulnerabilities being exploited with CVEs released back in 1999. So the lesson learned is make sure to audit for new and older vulnerabilities since any vulnerability is relevant! The next diagram shows the largest volume of vulnerabilities exploited had a CVE published back in 2007.
 Some good news is Mobile devices seem to be of low interest for breaches. The Verizon report claims its probably due to the platforms not being a preferred vector for data breaches represented by only 0.03% of new mobile malware seen by customers. Of this 0.03%, 96% was targeted at Android devices, which isn’t a surprised based on android’s open nature.
Some good news is Mobile devices seem to be of low interest for breaches. The Verizon report claims its probably due to the platforms not being a preferred vector for data breaches represented by only 0.03% of new mobile malware seen by customers. Of this 0.03%, 96% was targeted at Android devices, which isn’t a surprised based on android’s open nature.
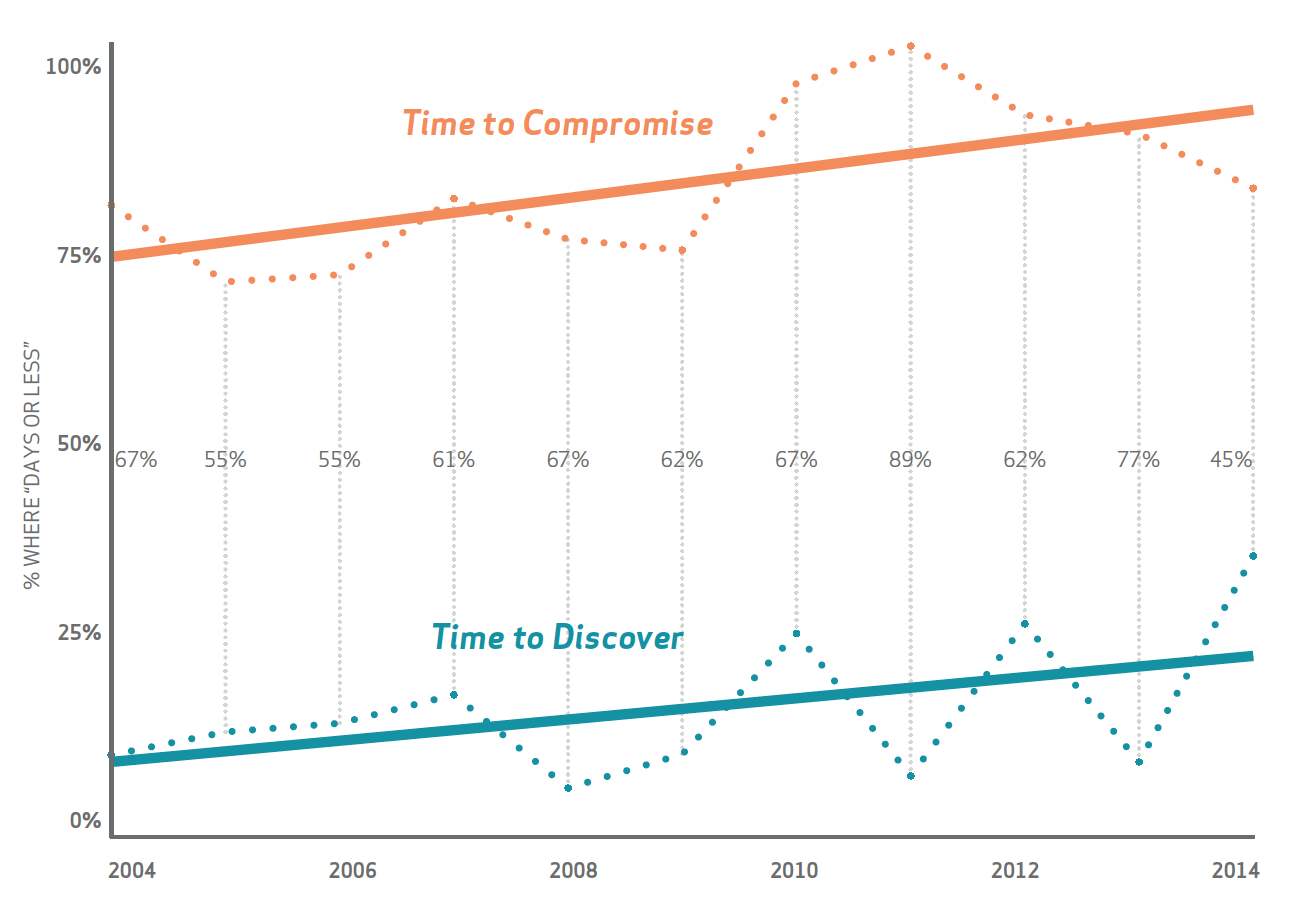
How effective are detection capabilities against breaches? The Verizon report shows half of the organizations discovered malware events during 35 of fewer days in 2014 (FYI 35 days is not good). Comparing detection verse compromise with a goal of detecting within a few days or less is still fairly low meaning organizations are taking too long to detect a breach. The next diagram represents this trend.
These are just a few points I found interesting in the report. One comment that stood out to me was after analyzing the volume of malware, the report claims averaging out the volume of malware seen means five malware events occur every second across all organizations studied. So basically 5 malware events just happened against a organization while you read the last few sentences.
Check out the report for more details on breaches seen last year. The data validates the question “if you KNOW you are going to be breached, would you do security differently?” Hopefully breach detection capabilities is part of your security strategy.