Cisco just released its annual Security Report that can be downloaded HERE. This report takes research, insights and perspectives from Cisco and other security experts such as Level 3 Threat Research labs. Topics covered are Threat Intelligence IE trends in web attack vectors, web attack methods and vulnerabilities , Industry Insights IE how the industry is doing, Security capabilities Benchmark Study IE security professional’s perceptions of the state of security and Looking Forward, which covers some case studies and updates on on research targeting reducing time to detection of threats.
Here is a list of some interesting highlights from this report:
It was great to see the Angler exploit kit go down (I posted about this HERE) however what is interesting is how fast it came back (here is a article on that HERE). Basically, the people behind these attacks are able to tweak things very quickly and get it back out there making it almost impossible to truly prevent these attacks from happening.
-
Cisco, with help from Level 3 Threat Research Labs and cooperation from the hosting provider Limestone Networks, identified and sidelined the largest Angler exploit kit operation in the United States, which was targeting 90,000 victims per day and generating tens of millions of dollars annually for the threat actors behind the campaign.
I found this one interesting being a fan of the Browser Exploitation Framework (BeEF) tool. Not only are browsers vulnerable, the auto installation of browser extensions IE crapware are causing people to get compromised. Remember to not quickly click through installing software or just download software from anywhere or you may get some malicious extras that expose you to bad stuff.
- Malicious browser extensions can be a major source of data leakage for businesses and are a widespread problem. We estimate that more than 85 percent of organizations studied are affected by malicious browser extensions.
Looks like Flash is still bad. Hopefully the reducing of risk will actually happen.
- Adobe Flash vulnerabilities continue to be popular with cybercriminals. However, software vendors are reducing the risk that users will be exposed to malware through Flash technology.
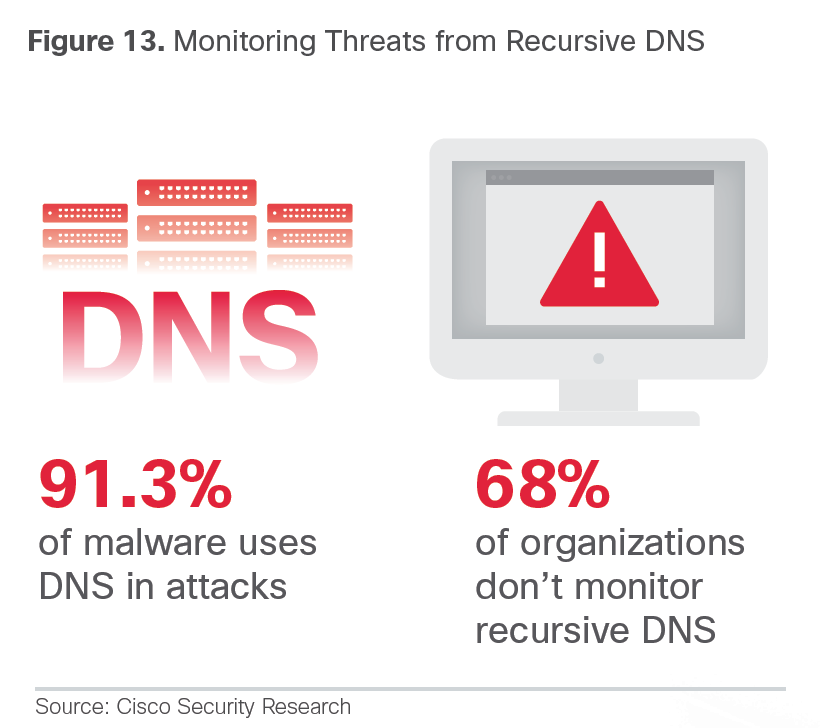
DNS seems to be something to leverage for security intelligence since the majority of malware is using it to carry out campaigns.
- Cisco’s analysis of malware validated as “known bad” found that the majority of that malware—91.3 percent— uses the Domain Name Service (DNS) to carry out campaigns. Through retrospective investigation into DNS queries, Cisco uncovered “rogue” DNS resolvers in use on customer networks. The customers were not aware that the resolvers were being used by their employees as part of their DNS infrastructure.
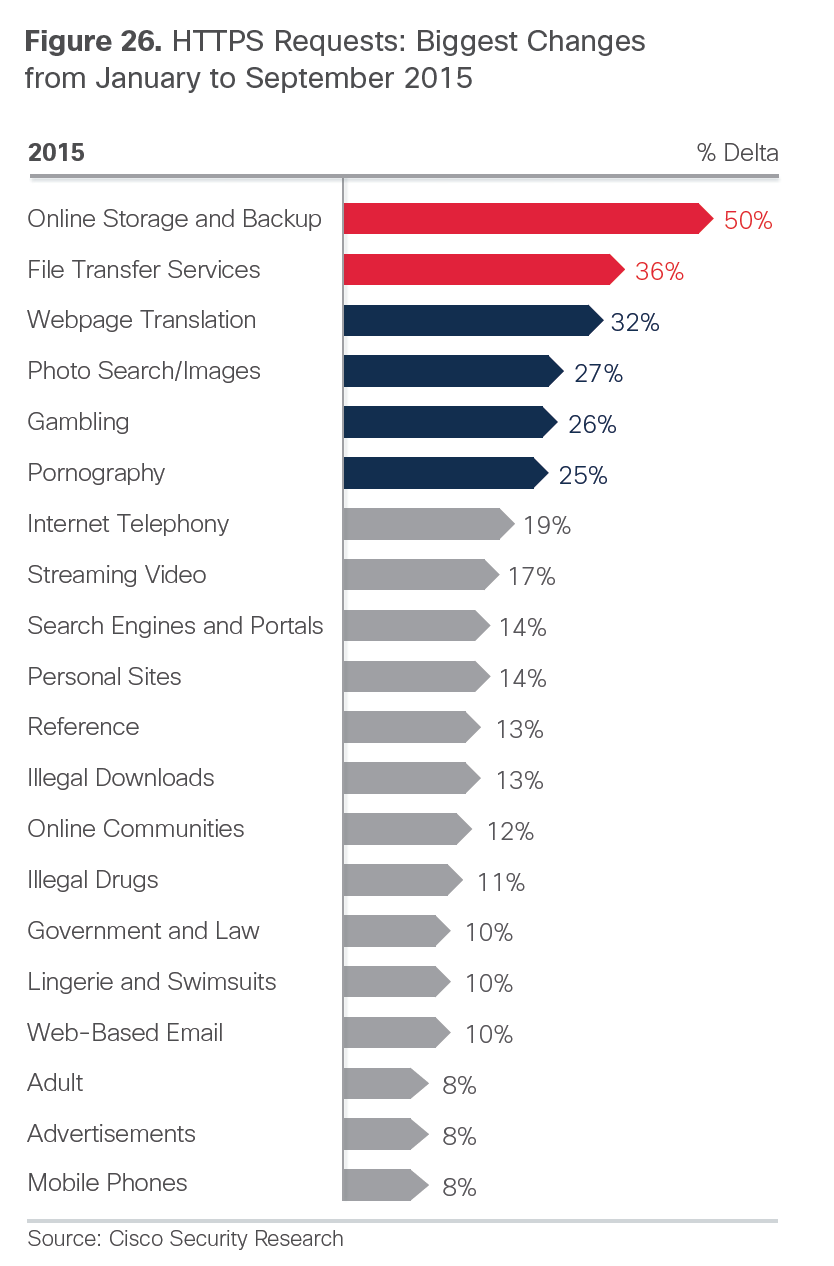
We all saw this coming. Now HTTPS is being seen more than HTTP. Go encryption however don’t think this is a security feature. Many malicious websites can hide as categories many customers tend to not decrypt such as banking or religion. We find it is common practice to do “selective decryption of SSL” and the attackers know this as well.
- Observing the trends in 2015, our researchers suggest that HTTPS encrypted traffic has reached a tipping point: it will soon become the dominant form of Internet traffic. Although encryption can help protect consumers, it also can undermine the effectiveness of security products, making it more difficult for the security community to track threats. Adding to the challenge, some malware may initiate encrypted communications across a diverse set of ports.
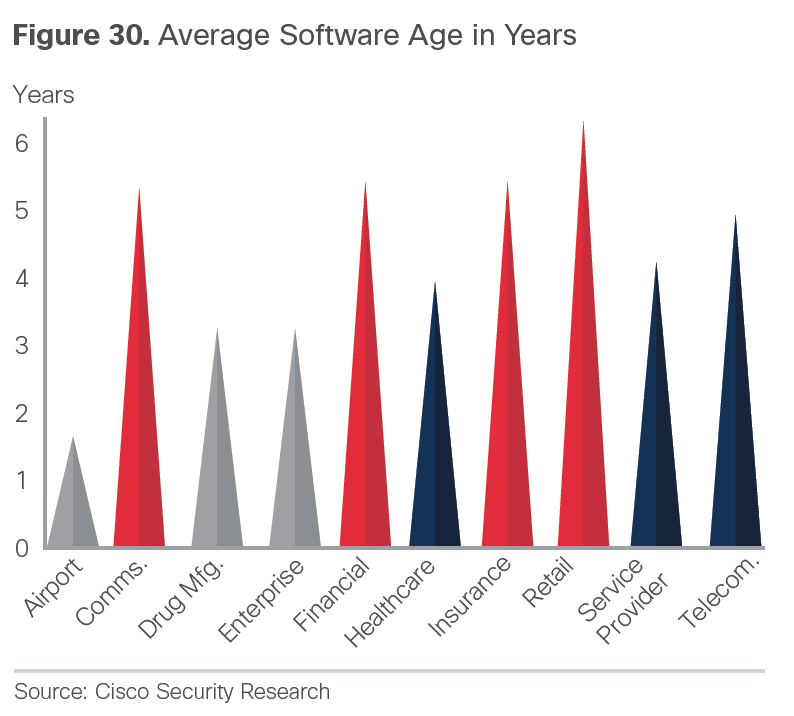
It shouldn’t be a shock that the majority of customers being evaluated during assessments have vulnerabilities due to old software and hardware.Yes, you fear the unknown day zeros however the majority of recorded breaches according to the Verizon Breach Report stated that 99% of the time, the vulnerability identified after a breach was known and a patch was available for over a year. This Cisco report backs up what the Verizon report found.
- Aging infrastructure is growing and leaves organizations increasingly vulnerable to compromise. We analyzed 115,000 Cisco® devices on the Internet and discovered that 92 percent of the devices in our sample were running software with known vulnerabilities. In addition, 31 percent of the Cisco devices in the field that were included in our analysis are “end of sale” and 8 percent are “end of life.”
This backs up the concept that small business continues to be the top target for attackers. Why is that? Well because they are the easiest targets. Also they are great pivoting points to launch attacks against larger targets.
- The benchmark study shows that small and midsize businesses (SMBs) use fewer defenses than larger enterprises. For example, 48 percent of SMBs said in 2015 that they used web security, compared to 59 percent in 2014. And 29 percent said they used patching and configuration tools in 2015, compared with 39 percent in 2014. Such weaknesses can place SMBs’ enterprise customers at risk, since attackers may more easily breach SMB networks.
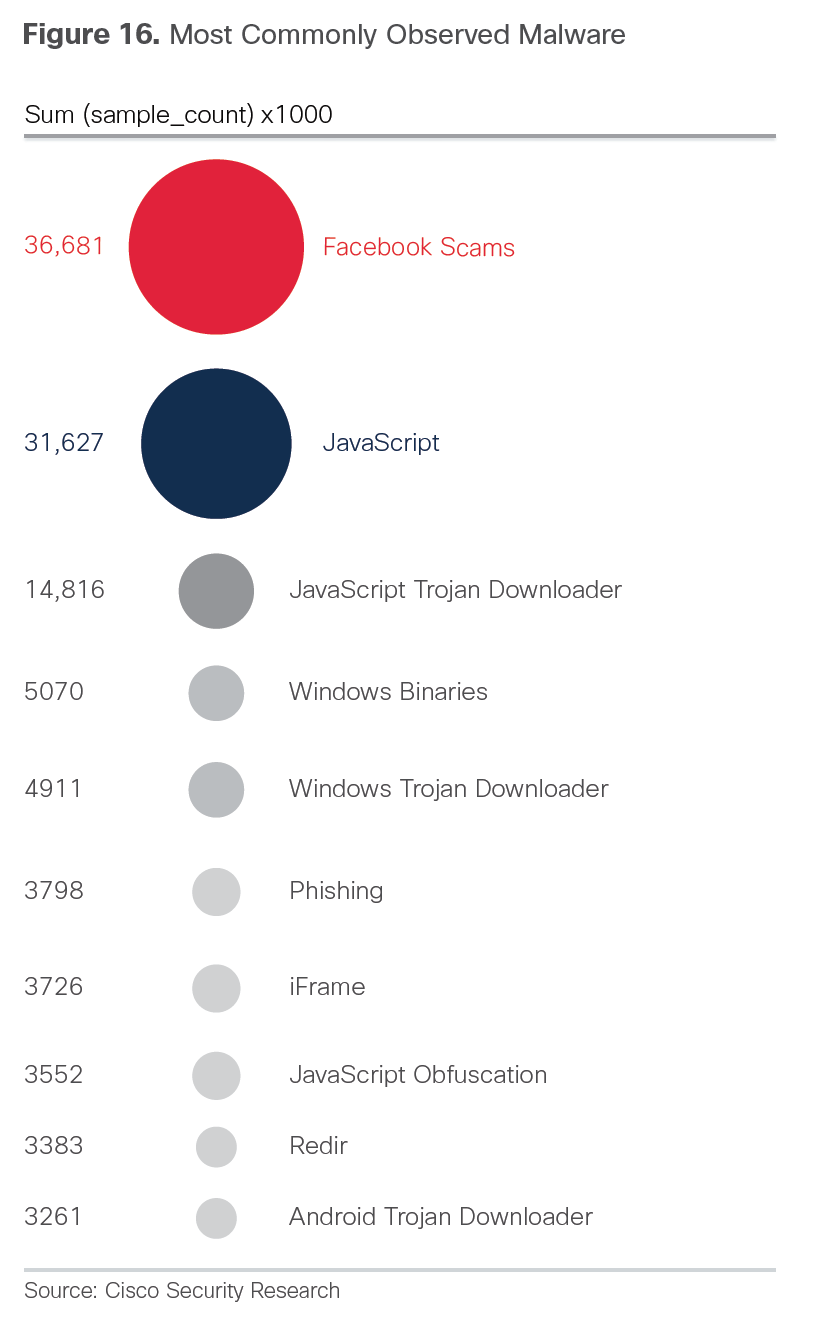
Outsourcing Security Services is increasing according the this research. 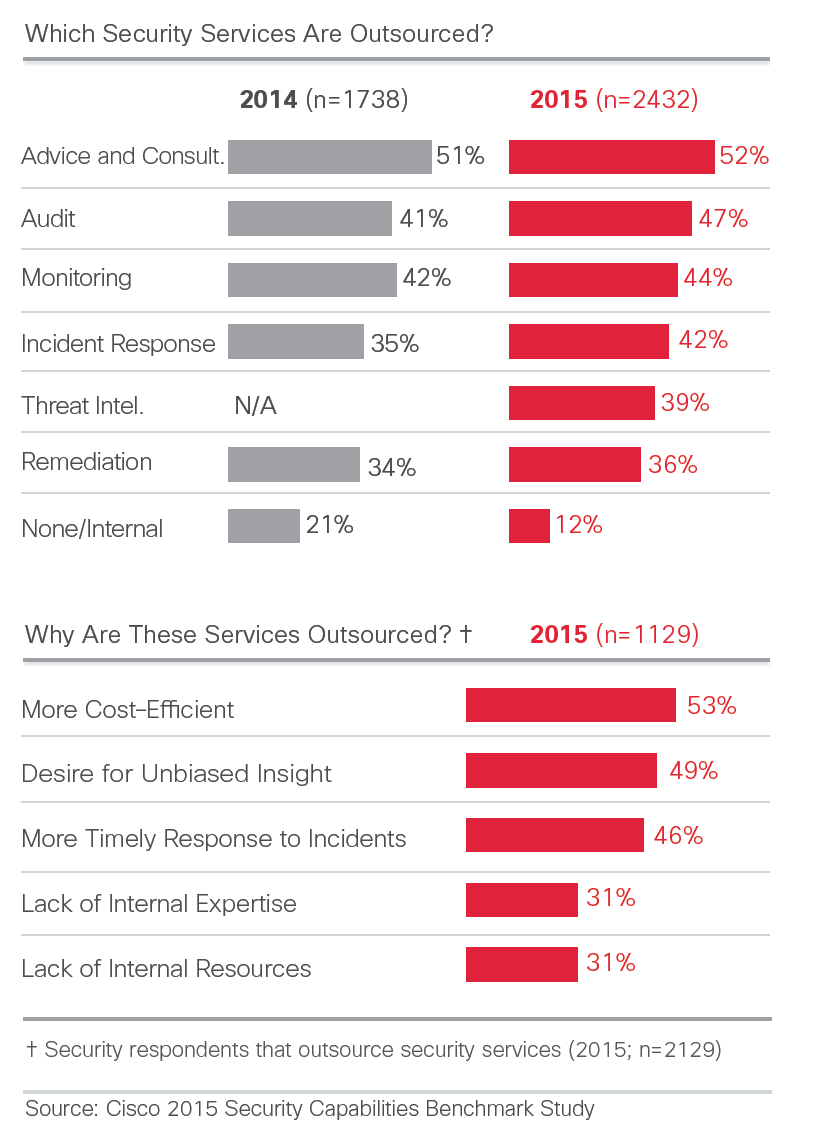 I like this diagram showcasing the most commonly observed malware. Not shocking to see Facebook scams at the top.
I like this diagram showcasing the most commonly observed malware. Not shocking to see Facebook scams at the top.
 That’s my summery. Check out the full report for more details on what I highlighted as well as other findings.
That’s my summery. Check out the full report for more details on what I highlighted as well as other findings.